The Cross-Site Scripting also known as XSS is a prevalent web security threat and one of the favorite method of attackers to steal your personal information. Cross-site scripting, which targets users, made up almost one-third of the total number of attacks.
In XSS, the web hackers add a malicious piece of codes in your Server Code. Whenever a client sends a request on your website, this code becomes a part of the client’s side and hackers can steal confidential information. Normally XSS victims are those websites that let users share data and contents e.g. Blogs etc. mlytics Enhanced Security feature includes a Web Application Firewall which can be used to mitigate the XSS risks.
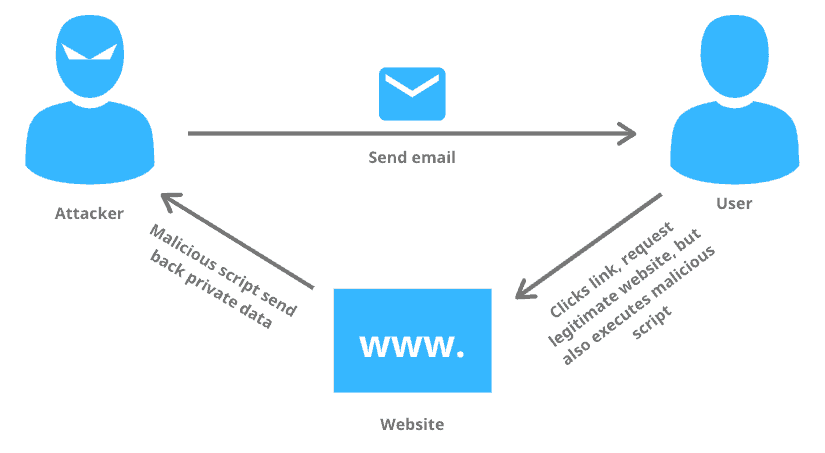
The Cross-Site Scripting consists of two types of attacks:
- Reflected cross-site scripting – the malicious code is added at the end of the URL of a legitimate website and when the victim loads the link into the browser, the web browser executes the malicious link.
- Persistent cross-site scripting – In this form of XSS, it lets users post content that others can see. For example, most of us came across the time when some of our friends complain about the presence of a suspicious link on our social media walls or in the form of messages sent to our friends by us and we have no idea when and how this happens. So, the Persistent XSS is behind the “strange” activity in which hacker impersonates us and send/post the malicious links.
How does it work?
The flow of a typical cross-site scripting attack is as follows:
- When the victim loads the webpage, the malicious code copies the important user data from cookies.
- The malicious code then sends the HTTP request to the attacker’s server with attached stolen cookies in the request’s body.
- The attacker can then use the stolen cookie information for identity theft and performing unauthorized actions on the behalf of the user’s credentials.
How to prevent cross-site scripting?
There is no one single strategy to avoid XSS attacks, meaning there is no one solution that fits all the scenarios. But, here are a few tips that you can use for protecting your website:
- Try not to send input in HTML forms.
- Always validate the input.
- Sanitize data
- Take proper security measures for protecting cookies information.
- Don’t save sensitive information e.g. don’t let the browser to remember the e-banking site’s password.
- Try tying the cookies to particular IP addresses so that cross-site scripting attackers cannot access them.
- Set the WAF rules. Apply proper WAF rules so that reflective XSS can also be prevented.
