A man-in-the-middle attack is a method which an attacker places himself in between the two devices and intercepts or modifies the messages/communication. The attacker is also able of impersonating as either of two agents and can do unauthorized actions. The attack needs three participants: the victim, the entity/system under attack and the middleman who eavesdrops.
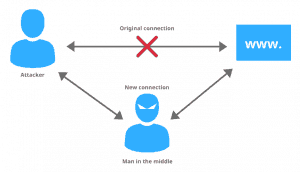
A good example would be an attacker sitting between a user and website and stealing the user’s credentials for illegal uses. The attacker is also able of impersonating as either of two agents and can do unauthorized actions.
These attacks can target email communications, DNS lookups, and public WiFi networks. Typical targets of man-in-the-middle attacks include SaaS businesses, e-commerce businesses, and users of financial apps. The financial apps are an important target because an attacker can perform illegal funds transactions and gains a lot of financial benefits within seconds.
How the attack is done?
A typical man-in-the-middle attack can be done by:
- Stealing Cookies
- Targeting the HTTP Connection between users and the website they want to visit
With the help of stolen cookies or stolen connection, the attacker is able to hijack the session and steal the user’s information and gain the ability to impersonate the victim.
Examples
An example of an offline man-in-the-middle attack is the interception of a letter by the mailman who either just reads its contents or even replaces its contents. One can visualize an online man-in-the-middle attack in a public place like a mall that provides free Wi-Fi connection available that has a wireless router with malicious software installed in it. If a user visits a bank’s website at that time from phone or laptop, he or she may end up losing bank credentials. These attacks can be caused because of the following reasons:
- ARP Cache Poisoning
- DNS Spoofing
- Session Hijacking
- SSL Hijacking
How to prevent a man-in-the-middle attack?
Since there are multiple ways to carry out a man-in-the-middle attack, so there is no one solution that can fit all the scenarios. One of the best ways to prevent man-in-the-middle attack is to use TSL protocol which enables secure communication between both parties but it can also be broken if a man-in-the-middle attack is too sophisticated.
The best option is to use the HTTPS protocol which blocks every unsecured connection. Authentication certificates can be used to prevent your system from a man-in-the-middle attack.
Email hijackings can be prevented by using Secure/Multipurpose Internet Mail Extension. The individual users can also protect them by not accessing their important accounts e.g. e-banking accounts on public Wi-Fi unless the Internet connections are not protected by Virtual Private Networks.
